场景:
公司A(Server)—IPSec—公司B(Server)–公司B其他公网主机
公司A IPSec VPN Server 公网IP:103.1.1.1 内网段10.255.203.0/24
公司B IPSec VPN Server 公网IP:116.1.1.1 内网段10.0.0.0/24
实现效果:公司A Server 可以与公司B公网主机互相访问
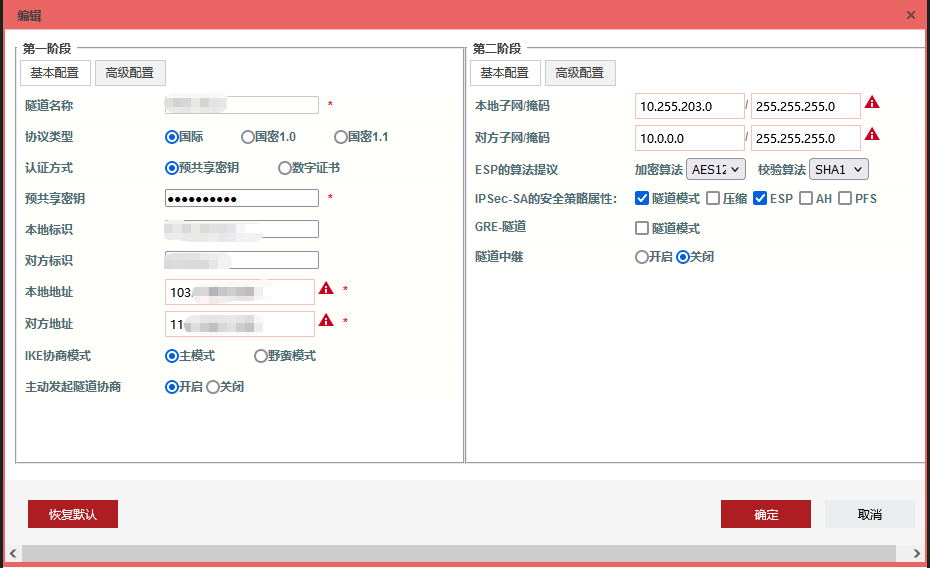
公有云VPN连接不支持本地标识、对方标识修改,默认是IPv4地址,所以没法使用,只能在物理机上安装Strongswan来实现对接,site-to-site vpn连接后,本机ip a是看不到虚拟网卡的,也不需要分配内网互联IP,连接成功后路由表里也是看不到的,需要通过ipsec命令查看
# yum install strongswan
# more /etc/strongswan/ipsec.conf | grep -v "#\|^$"
config setup
strictcrlpolicy=no
charondebug = "all"
uniqueids = yes
nat_traversal=yes
conn hb-drms-ipsec
auto=route
authby=secret
left=103.1.1.1
leftid="beijing@test"
right=116.1.1.1
rightid="duck@test"
leftsubnet=10.205.203.0/24
rightsubnet=10.0.0.0/24
type=tunnel
leftauth=psk
rightauth=psk
keyexchange=ikev1
ikelifetime=24h
ike=aes128-sha1-modp1024
esp=aes128-sha1-modp1024
lifetime=1h
keyingtries=%forever
dpddelay=30s
dpdtimeout=300s
dpdaction=restart
# more /etc/strongswan/ipsec.secrets
# ipsec.secrets - strongSwan IPsec secrets file
103.1.1.1 116.1.1.1 : PSK "xxxx"
beijing@test duck@test : PSK "xxxx"
# more /export/sh/ipip-tunnel/set-up-drms.sh
#!/usr/bin/env bash
ip tunnel add hb-drms1 mode ipip remote 198.1.1.2 local 116.1.1.1 ttl 255
ip addr add 10.0.0.254/32 peer 10.0.0.253/32 dev hb-drms1
ip link set hb-drms1 up
ip route add 10.0.0.11 via 10.0.0.253 dev hb-drms1
ip tunnel add hb-drms2 mode ipip remote 198.1.1.3 local 116.1.1.1 ttl 255
ip addr add 10.0.0.252/32 peer 10.0.0.251/32 dev hb-drms2
ip link set hb-drms2 up
ip route add 10.0.0.14 via 10.0.0.251 dev hb-drms2
iptables放行
iptables -A INPUT -p udp -s 103.1.1.1/32 -j ACCEPT
iptables -A OUTPUT -p udp -d 103.1.1.1/32 -j ACCEPT
iptables -A INPUT -p 50 -s 103.1.1.1/32 -j ACCEPT
iptables -A INPUT -p 51 -s 103.1.1.1/32 -j ACCEPT
iptables -A OUTPUT -p 50 -d 103.1.1.1/32 -j ACCEPT
iptables -A OUTPUT -p 51 -d 103.1.1.1/32 -j ACCEPT
# ipip allow
iptables -A INPUT -i eth0 -p 4 -s 198.1.1.1/32 -d 116.1.1.1/32 -j ACCEPT
iptables -A OUTPUT -o eth0 -p 4 -s 116.1.1.1/32 -d 198.1.1.1/32 -j ACCEPT
...
iptables -A INPUT -i hb-drms+ -j ACCEPT
iptables -A OUTPUT -o hb-drms+ -j ACCEPT
iptables -A FORWARD -i hb-drms+ -o eth0 -j ACCEPT
iptables -A FORWARD -i eth0 -o hb-drms+ -j ACCEPT
云主机上配置
ip tunnel add bj-test mode ipip remote 116.1.1.1 local 10.0.0.11 ttl 255
ip addr add 10.0.0.253 peer 10.0.0.254 dev bj-test
ip link set bj-test up
ip route add 10.255.203.0/24 via 100.0.0.254 dev bj-test
ip tunnel add bj-test mode ipip remote 116.1.1.1 local 10.0.0.14 ttl 255
ip addr add 10.0.0.251 peer 10.0.0.252 dev bj-test
ip link set bj-test up
ip route add 10.255.203.0/24 via 10.0.0.252 dev bj-test
ipsec vpn连接成功后,要看到Routed Connections才行
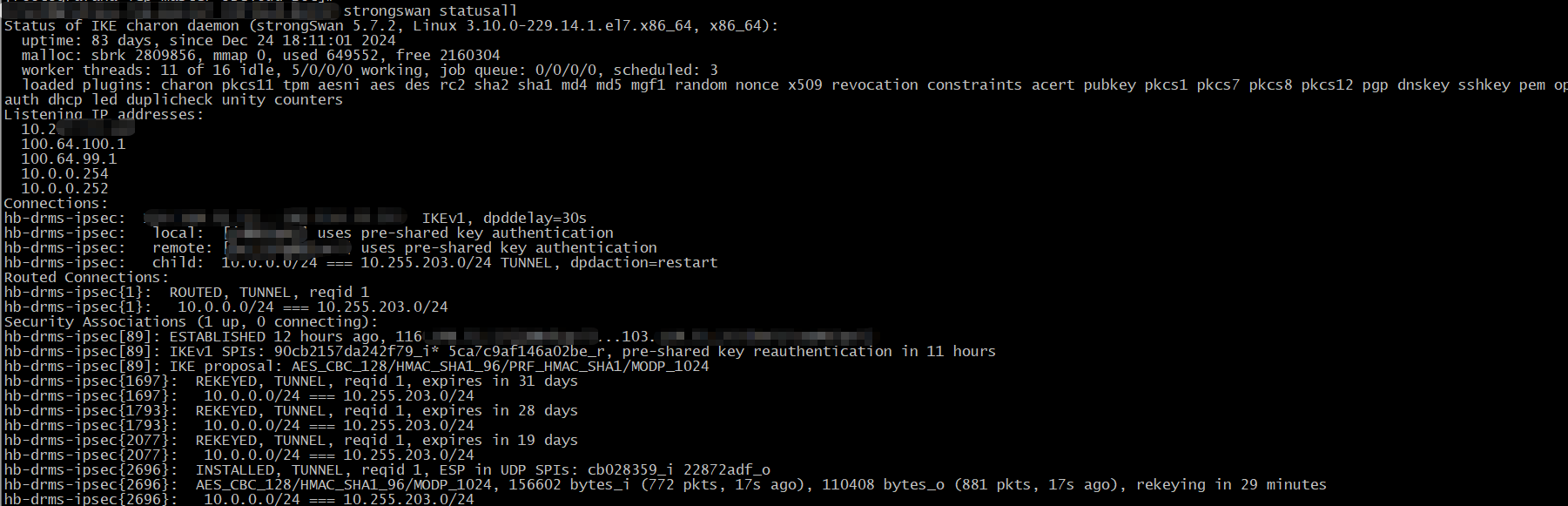
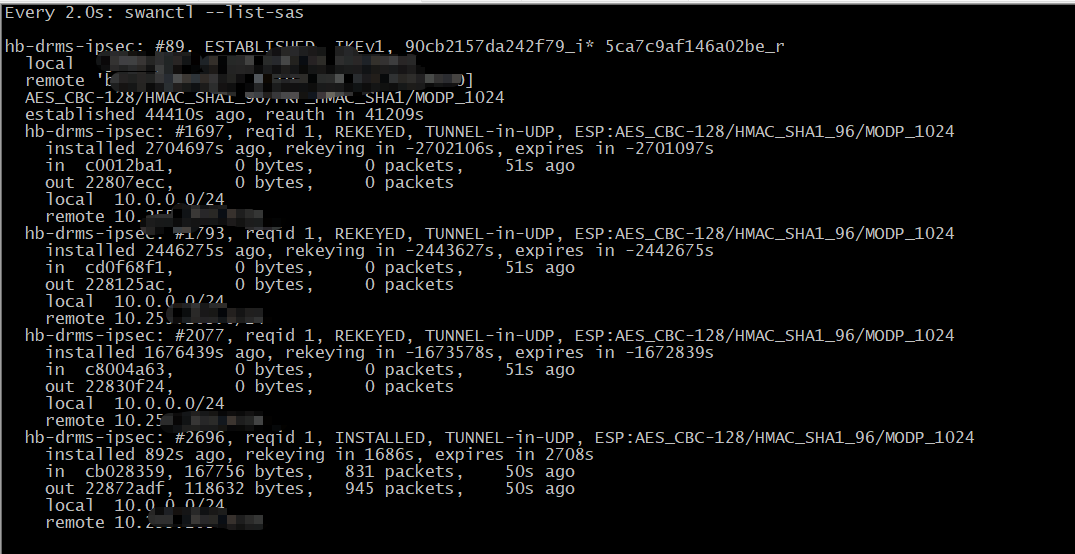
查看ipsec转发流量
watch swanctl –list-sas
公司B IPSec Server上测试,可以访问公司A的Server
# ping 10.255.203.254 -I 10.0.0.252
PING 10.255.203.254 (10.255.203.254) from 10.0.0.252 : 56(84) bytes of data.
64 bytes from 10.255.203.254: icmp_seq=1 ttl=63 time=13.3 ms
64 bytes from 10.255.203.254: icmp_seq=2 ttl=63 time=4.22 ms
64 bytes from 10.255.203.254: icmp_seq=3 ttl=63 time=4.12 ms
64 bytes from 10.255.203.254: icmp_seq=4 ttl=63 time=8.59 ms